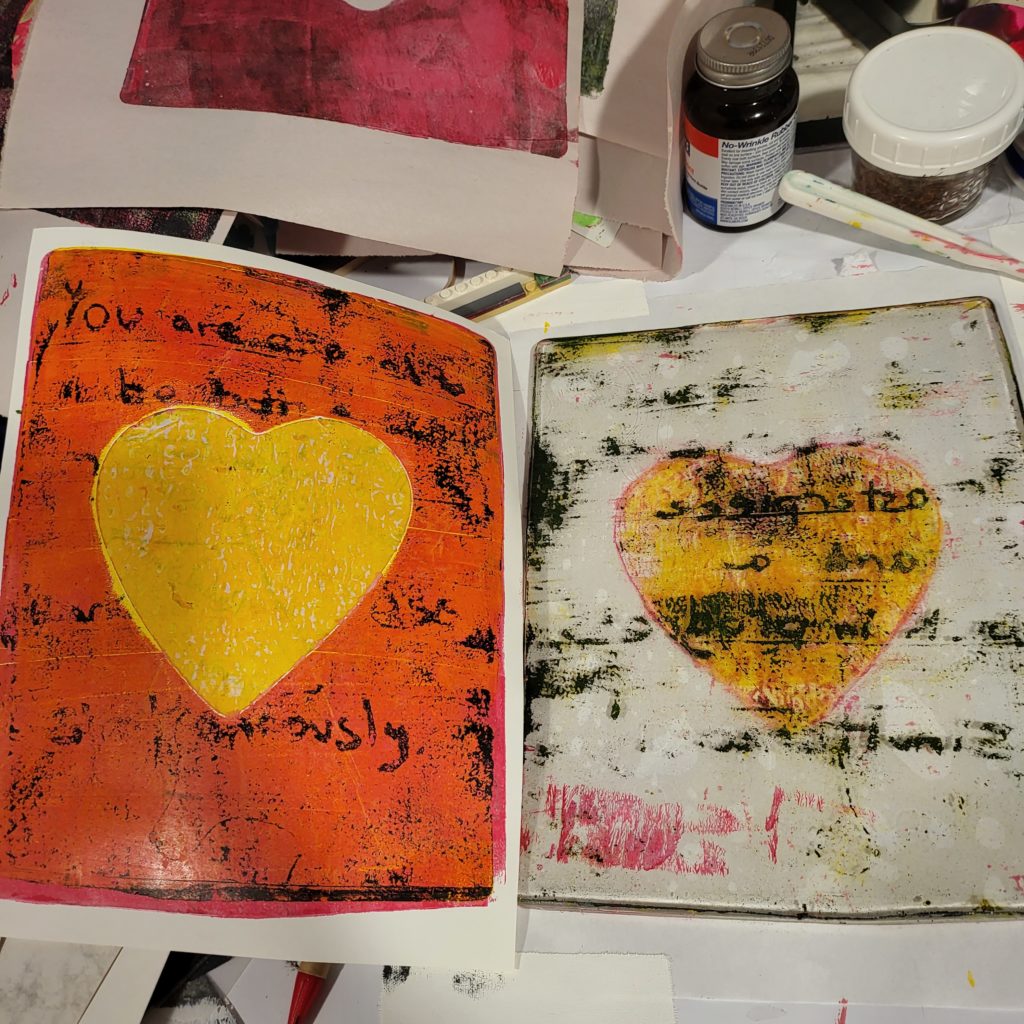I love hamentaschen – a traditional holiday filled cookie – for so many reasons. The mathematics of turning a mostly flat circle into a 3-sided pyramid. The effort of pinching the points, the glorious feeling when the cookies come out of the oven and look great. The social aspects of giving hamentaschen away and baking with friends. The flavor combinations – including savory hamentaschen. And, I mean, it’s a cookie…I love cookies!

As much as preparing food fulfills my desire to provide comfort and nourishment for myself and others, there’s always a background process asking, “how can I make this better?” This is a concept familiar to product managers and engineers alike; my iterative development process is not limited to the computing realm.
Welcome to my kitchen, where culinary craftsmanship meets the art of optimization.
One challenge of holiday baking is that lessons learned can get lost in the flurry of activity and to-do lists. It’s easy to forget previous learnings. Stressful situations like more people than originally planned or too many items for the oven have lead to experiments where I figure out which brisket is more flavorful and fall-off-the-fork delicious – baked in the oven or the slow cooker? (Answer: surprisingly, the oven!)
To combat this challenge, I heavily annotate and change recipes, and keep menu plans with notes of quantities, number of guests, and how well everything worked out.
Holiday food preparation is especially prone to the Pot Roast principle
(reference: https://www.psychologytoday.com/us/blog/thinking-makes-it-so/201402/the-pot-roast-principle). The process is infused with stress – we are usually preparing several dishes, to meet a specific deadline. We don’t have time to question what’s the most efficient use of our time, resources, or even oven space. We may take for granted that a certain food has to be cooked on a stove or in an oven, or even that we should prepare it the same day we eat it.

Another challenge is that often, holiday food preparation can be chaotic because there are multiple dishes to make. I don’t do a big Purim feast (though maybe I will in the future). I especially love Hamentaschen for experimentation because it’s the only recipe I’m making. I have the time and the space to think, “how can I make this better?” and “What about this is really working for me?”
One effect of baking Hamentaschen only once a year is that the iterative process has a long cycle. For example, I prefer a more “open” hamentaschen, where you can see the filling. I learned this after too many years of eating mystery-filled cookies….I like to know what I’m getting into! I don’t like the mystery; if want raspberry and I get chocolate it’s disappointing.

There are so many minor variables that can be changed, and with less frequency, it takes a while to tweak the variables exactly how I like them. For example – many people use jam, or chocolate chips to fill their cookies. I personally don’t like how jam reduces and is sticky, and how chocolate chips are a very dry filling on what is usually a dry, crumbly cookie. In fact, I don’t like a shortbread-style, crumbly cookie for hamentaschen.
For the 20 years I’ve owned the process of baking hamentaschen – e.g. not baking with someone else who dictates the process. I’m still innovating and changing things after all this time, because when you make something once a year, the iterative cycle is long. Interestingly, I’ve not done much experimentation with the dough itself. My family’s recipe uses some orange juice, which solves the problem of a flavorless sweet dough. And my twin brother long ago tripled the amount of butter from our mother’s recipe so the dough is not crumbly.
In addition, inviting people over to make the cookies is not just a fun activity to do with friends. Some of my friends have never made hamentaschen and it’s a lesson in how much of a learning curve making these cookies are. As a product manager, I have to balance being an expert in my product, with working with people who inherently are NOT experts in the product. As a hamentaschen baker, I have to explain to friends how thin to roll out the dough, how big or small of a circle to cut, how much filling to put in, how to make the shape, and how to pinch the edges closed. And of course, how variations in each of those steps change the cookie – some of those changes are objectively “good” or “bad”, but many are personal preference.
The process really brings me back to beginner mindset, reminding me that something I’m an expert in feels easy to me because I have lots of experience in it. For folks who haven’t developed the same experience over years, learning all the details can be overwhelming when they just wanted to come over and bake cookies. Audience expectation and management are important skills!
Bakers try to make sure their hamentaschen hold their shape and don’t flatten. Through the years, I have come to realize that the filling is as important as the dough itself. Chocolate chips are often used as filling, but I find them too dry and hard after baking. I prefer a more brownie-like chocolate filling. While it is popular to use jam or jelly as filling, I personally don’t like that those fillings. They have a tendency to reduce while cooking, which means the end product has less filling, and a different dough-to-filling ratio than I like. Jams and jellies also become watery when heated, so leaks are more prevalent. And I just don’t like the sticky texture of those fillings when cooked.
And it wasn’t until this year that I realized that a filling that does not reduce, has a great side effect – it helps the hamentaschen hold their shape better. So even if the dough flattens a bit, or the edges aren’t pinched well and open, there is no leakage.

Poppy seed filling is traditional, but also one of my favorites. I prefer the Solo brand poppy seed cake and pie filling, where the poppyseeds are combined with just enough of a sticky sweet syrup to hold together. In my area, this filling is most prevalently found in December, so I buy what I need then, otherwise I can’t always find it in the grocery store in February or March when I want it. This is the kind of optimization I do, learned after many years – I buy my hamentaschen filling a few months ahead of time!
One problem my family has had in eating the cookies, is that I like to make both chocolate filled hamentaschen and poppy seed filled hamentaschen. Sometimes it’s hard to tell the difference. This year I got the great idea to fill the poppyseed cookies last, and mix some poppyseeds into the dough so that it is very clear which cookies have poppyseeds and which do not. I lament that it took me over 20 years to come up with this stroke of genius, but it’s to be expected when I only bake hamentaschen once a year.
So, now that this year’s hamentaschen baking is over, what next? I’ve written down my idea for next year. See, my dough recipe makes 4 dozen cookies (cut to 3 inch circles), but the cans of pie filling and my chocolate filling recipe makes enough to fill 3 dozen cookies. It’s not the math that’s difficult, I can multiply by 3/4, but I want to keep some standard measurements – 1/4 cup of orange juice nicely changes into 3 tbsp, but the butter comes out to 153 grams, or 10.8 tablespoons, or 1.35 sticks. None of these are useful for me, so I’ll work on standardizing the recipe without losing any of the characteristics I love about the dough.
Fewer than 1% of meals are holiday meals. Is it ridiculous to optimize, solve challenges, be so attentive to detail, and innovate on something that only happens rarely? Maybe, but that’s just how I am.